This article is about macro security and explains the risks of enabling macros and how the
Trust Center in the 2007 Microsoft Office system can help to mitigate these risks.
What is a macro and what is the security risk?
Macros automate frequently-used tasks; many are created with VBA
(Visual Basic for Applications (VBA): A macro-language version of Microsoft Visual Basic that is used to program Microsoft Windows-based applications and is included with several Microsoft programs.) and are written by software developers. However, some macros pose a potential security risk. A person with malicious intent can introduce a destructive macro, in a document or file, which can spread a virus
(virus: A computer program or macro that "infects" computer files by inserting copies of itself into those files. When the infected file is loaded into memory, the virus can infect other files. Viruses often have harmful side effects.) on your computer.
Enable or disable macros with the Trust Center
Macro security settings are located in the Trust Center. However, if you work in an organization, your system administrator might have changed the default settings to prevent anyone from changing any settings.
Note When you change your macro settings in the Trust Center, they are changed only for the Office program that you are currently using. The macro settings are not changed for all your Office programs.
Which program are you using?
Access
- Click the Microsoft Office Button
 , and then click Access Options.
, and then click Access Options.
- Click Trust Center, click Trust Center Settings, and then click Macro Settings.
- Click the options that you want:
- Disable all macros without notification Click this option if you don't trust macros. All macros in documents and security alerts about macros are disabled. If there are documents with unsigned macros that you do trust, you can put those documents into a trusted location. Documents in trusted locations are allowed to run without being checked by the Trust Center security system.
- Disable all macros with notification This is the default setting. Click this option if you want macros to be disabled, but you want to get security alerts if there are macros present. This way, you can choose when to enable those macros on a case by case basis.
- Disable all macros except digitally signed macros This setting is the same as the Disable all macros with notification option, except that if the macro is digitally signed by a trusted publisher, the macro can run if you have already trusted the publisher. If you have not trusted the publisher, you are notified. That way, you can choose to enable those signed macros or trust the publisher. All unsigned macros are disabled without notification.
- Enable all macros (not recommended, potentially dangerous code can run) Click this option to allow all macros to run. This setting makes your computer vulnerable to potentially malicious code and is not recommended.
Excel
- Click the Microsoft Office Button
 , and then click Excel Options.
, and then click Excel Options.
- Click Trust Center, click Trust Center Settings, and then click Macro Settings.
- Click the options that you want:
- Disable all macros without notification Click this option if you don't trust macros. All macros in documents and security alerts about macros are disabled. If there are documents with unsigned macros that you do trust, you can put those documents into a trusted location. Documents in trusted locations are allowed to run without being checked by the Trust Center security system.
- Disable all macros with notification This is the default setting. Click this option if you want macros to be disabled, but you want to get security alerts if there are macros present. This way, you can choose when to enable those macros on a case by case basis.
- Disable all macros except digitally signed macros This setting is the same as the Disable all macros with notification option, except that if the macro is digitally signed by a trusted publisher, the macro can run if you have already trusted the publisher. If you have not trusted the publisher, you are notified. That way, you can choose to enable those signed macros or trust the publisher. All unsigned macros are disabled without notification.
- Enable all macros (not recommended, potentially dangerous code can run) Click this option to allow all macros to run. This setting makes your computer vulnerable to potentially malicious code and is not recommended.
- Trust access to the VBA project object model This setting is for developers and is used to deliberately lock out or allow programmatic access to the VBA object model from any Automation client. In other words, it provides a security option for code that is written to automate an Office program and programmatically manipulate the Microsoft Visual Basic for Applications (VBA) environment and object model. This is a per user and per application setting, and denies access by default. This security option makes it more difficult for unauthorized programs to build "self-replicating" code that can harm end-user systems. For any Automation client to be able to access the VBA object model programmatically, the user running the code must explicitly grant access. To turn on access, select the check box.
Tip You can open the macro security settings dialog box from the
Developer tab in the Ribbon, which is part of the Microsoft Office Fluent user interface. If the
Developer tab is not available, click the
Microsoft Office Button
, and then click
Excel Options. Click
Popular, and then select the
Show Developer tab in the Ribbon check box.
Outlook
- On the Tools menu, click Trust Center.
- Click Macro Settings.
- Click the options that you want:
- No warnings and disable all macros Click this option if you don't trust macros. All macros and security alerts about macros are disabled.
- Warnings for signed macros; all unsigned macros are disabled This is the default setting and is the same as the Disable all macros with notification option, except that if the macro is digitally signed by a trusted publisher, the macro can run if you have already trusted the publisher. If you have not trusted the publisher, you are notified. That way, you can choose to enable those signed macros or trust the publisher. All unsigned macros are disabled without notification.
- Warnings for all macros Click this option if you want macros to be disabled, but you want to get security alerts if there are macros present. This way, you can choose when to enable those macros on a case by case basis.
- No security check for macros (Not recommended) Click this option to allow all macros to run. This setting makes your computer vulnerable to potentially malicious code and is not recommended.
PowerPoint
- Click the Microsoft Office Button
 , and then click PowerPoint Options.
, and then click PowerPoint Options.
- Click Trust Center, click Trust Center Settings, and then click Macro Settings.
- Click the options that you want:
- Disable all macros without notification Click this option if you don't trust macros. All macros in documents and security alerts about macros are disabled. If there are documents with unsigned macros that you do trust, you can put those documents into a trusted location. Documents in trusted locations are allowed to run without being checked by the Trust Center security system.
- Disable all macros with notification This is the default setting. Click this option if you want macros to be disabled, but you want to get security alerts if there are macros present. This way, you can choose when to enable those macros on a case by case basis.
- Disable all macros except digitally signed macros This setting is the same as the Disable all macros with notification option, except that if the macro is digitally signed by a trusted publisher, the macro can run if you have already trusted the publisher. If you have not trusted the publisher, you are notified. That way, you can choose to enable those signed macros or trust the publisher. All unsigned macros are disabled without notification.
- Enable all macros (not recommended, potentially dangerous code can run) Click this option to allow all macros to run. This setting makes your computer vulnerable to potentially malicious code and is not recommended.
- Trust access to the VBA project object model This setting is for developers and is used to deliberately lock out or allow programmatic access to the VBA object model from any Automation client. In other words, it provides a security option for code that is written to automate an Office program and programmatically manipulate the Microsoft Visual Basic for Applications (VBA) environment and object model. This is a per user and per application setting, and denies access by default. This security option makes it more difficult for unauthorized programs to build "self-replicating" code that can harm end-user systems. For any Automation client to be able to access the VBA object model programmatically, the user running the code must explicitly grant access. To turn on access, select the check box.
Tip You can open the macro security settings dialog box from the
Developer tab in the Ribbon, which is part of the Microsoft Office Fluent user interface. If the
Developer tab is not available, click the
Microsoft Office Button
, and then click
PowerPoint Options. Click
Popular, and then select the
Show Developer tab in the Ribbon check box.
Publisher
- On the Tools menu, click Trust Center.
- Click Macro Settings.
- Click the options that you want:
- Disable all macros without notification Click this option if you don't trust macros. All macros in documents and security alerts about macros are disabled. If there are documents with unsigned macros that you do trust, you can put those documents into a trusted location. Documents in trusted locations are allowed to run without being checked by the Trust Center security system.
- Disable all macros with notification This is the default setting. Click this option if you want macros to be disabled, but you want to get security alerts if there are macros present. This way, you can choose when to enable those macros on a case by case basis.
- Disable all macros except digitally signed macros This setting is the same as the Disable all macros with notification option, except that if the macro is digitally signed by a trusted publisher, the macro can run if you have already trusted the publisher. If you have not trusted the publisher, you are notified. That way, you can choose to enable those signed macros or trust the publisher. All unsigned macros are disabled without notification.
- Enable all macros (not recommended, potentially dangerous code can run) Click this option to allow all macros to run. This setting makes your computer vulnerable to potentially malicious code and is not recommended.
- Trust access to the VBA project object model This setting is for developers and is used to deliberately lock out or allow programmatic access to the VBA object model from any Automation client. In other words, it provides a security option for code that is written to automate an Office program and programmatically manipulate the Microsoft Visual Basic for Applications (VBA) environment and object model. This is a per user and per application setting, and denies access by default. This security option makes it more difficult for unauthorized programs to build "self-replicating" code that can harm end-user systems. For any Automation client to be able to access the VBA object model programmatically, the user running the code must explicitly grant access. To turn on access, select the check box.
Visio
- On the Tools menu, click Trust Center.
- Click Macro Settings.
- Click the options that you want:
- Disable all macros without notification Click this option if you don't trust macros. All macros in documents and security alerts about macros are disabled. If there are documents with unsigned macros that you do trust, you can put those documents into a trusted location. Documents in trusted locations are allowed to run without being checked by the Trust Center security system.
- Disable all macros with notification This is the default setting. Click this option if you want macros to be disabled, but you want to get security alerts if there are macros present. This way, you can choose when to enable those macros on a case by case basis.
- Disable all macros except digitally signed macros This setting is the same as the Disable all macros with notification option, except that if the macro is digitally signed by a trusted publisher, the macro can run if you have already trusted the publisher. If you have not trusted the publisher, you are notified. That way, you can choose to enable those signed macros or trust the publisher. All unsigned macros are disabled without notification.
- Enable all macros (not recommended, potentially dangerous code can run) Click this option to allow all macros to run. This setting makes your computer vulnerable to potentially malicious code and is not recommended.
- Trust access to the VBA project object model This setting is for developers and is used to deliberately lock out or allow programmatic access to the VBA object model from any Automation client. In other words, it provides a security option for code that is written to automate an Office program and programmatically manipulate the Microsoft Visual Basic for Applications (VBA) environment and object model. This is a per user and per application setting, and denies access by default. This security option makes it more difficult for unauthorized programs to build "self-replicating" code that can harm end-user systems. For any Automation client to be able to access the VBA object model programmatically, the user running the code must explicitly grant access. To turn on access, select the check box.
Word
- Click the Microsoft Office Button
 , and then click Word Options.
, and then click Word Options.
- Click Trust Center, click Trust Center Settings, and then click Macro Settings.
- Click the options that you want:
- Disable all macros without notification Click this option if you don't trust macros. All macros in documents and security alerts about macros are disabled. If there are documents with unsigned macros that you do trust, you can put those documents into a trusted location. Documents in trusted locations are allowed to run without being checked by the Trust Center security system.
- Disable all macros with notification This is the default setting. Click this option if you want macros to be disabled, but you want to get security alerts if there are macros present. This way, you can choose when to enable those macros on a case by case basis.
- Disable all macros except digitally signed macros This setting is the same as the Disable all macros with notification option, except that if the macro is digitally signed by a trusted publisher, the macro can run if you have already trusted the publisher. If you have not trusted the publisher, you are notified. That way, you can choose to enable those signed macros or trust the publisher. All unsigned macros are disabled without notification.
- Enable all macros (not recommended, potentially dangerous code can run) Click this option to allow all macros to run. This setting makes your computer vulnerable to potentially malicious code and is not recommended.
- Trust access to the VBA project object model This setting is for developers and is used to deliberately lock out or allow programmatic access to the VBA object model from any Automation client. In other words, it provides a security option for code that is written to automate an Office program and programmatically manipulate the Microsoft Visual Basic for Applications (VBA) environment and object model. This is a per user and per application setting, and denies access by default. This security option makes it more difficult for unauthorized programs to build "self-replicating" code that can harm end-user systems. For any Automation client to be able to access the VBA object model programmatically, the user running the code must explicitly grant access. To turn on access, select the check box.
Tip You can open the macro security settings dialog box from the
Developer tab in the Ribbon, which is part of the Microsoft Office Fluent user interface. If the
Developer tab is not available, click the
Microsoft Office Button
, and then click
Word Options. Click
Popular, and then select the
Show Developer tab in the Ribbon check box.
How can the Trust Center help protect me from unsafe macros?
Before enabling a macro in a document, the Trust Center checks for the following information:
- The macro is signed by the developer with a digital signature (digital signature: An electronic, encryption-based, secure stamp of authentication on a macro or document. This signature confirms that the macro or document originated from the signer and has not been altered.).
- The digital signature is valid (valid: Refers to the status of a certificate checked against a certificate authority's database and found to be legitimate, current, and not expired or revoked. Documents signed by a valid certificate and not altered since signing are considered valid.).
- This digital signature is current (not expired).
- The certificate associated with the digital signature was issued by a reputable certificate authority (CA) (certificate authority (CA): A commercial organization that issues digital certificates, keeps track of who is assigned to a certificate, signs certificates to verify their validity, and tracks which certificates are revoked or expired.).
- The developer who signed the macro is a trusted publisher (trusted publisher: The developer of a macro that is trusted by you on your computer. The trusted publisher is identified by the certificate that they used to digitally sign the macro. Also known as a trusted source.).
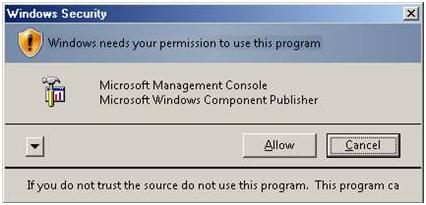
If the Trust Center detects a problem with any of these, the macro is disabled by default, and the Message Bar appears to notify you of a potentially unsafe macro.

To enable the macro click
Options on the Message Bar, a security dialog box opens. See the next section for information about making decisions about macros and security.
Note In Microsoft Office Outlook 2007 and Microsoft Office Publisher 2007, security alerts appear in dialog boxes, not in the Message Bar.
A security warning asks if I want to enable or disable a macro. What should I do?
When the Securty Options dialog appears, you can enable the macro or leave it disabled. You should enable the macro if you are sure it is from a trustworthy source.
 Important
Important If you are sure the document and macro are from a trustworthy source and have a valid signature, and you do not want to be notified about them again, instead of changing the default Trust Center settings to a less safe macro security setting, you can click
Trust all documents from this publisher in the security dialog box. This adds the publisher to your
Trusted Publishers list in the Trust Center. All software from that publisher is trusted. In the case where the macro doesn't have a valid signature, but you trust it and don't want to be notified again, instead of changing the default Trust Center settings to a less safe macro security setting, it is better to move the document to a
trusted location. Documents in trusted locations are allowed to run without being checked by the Trust Center security system.
Depending on the situation, the security dialog box describes the specific problem. The following table lists the possible problems and offers advice on what you should or should not do in each case.































 , and then click Access Options.
, and then click Access Options.